Pimp (or Bloat) Your Browser with Add-Ons
Every time you install another add-on in Firefox, you make it just a little more bloated and a bit slower. For that reason, it's important to pick your add-ons carefully. Add-ons are one of Firefox's best features because they allow you to create a browser with the features that you want. Although they slow the startup process and make Firefox consume more memory, selecting the best add-ons will save time, not cost time.
Now that I'm running Firefox on a 64-bit operating system, startup time is no longer an issue. You haven't heard a complaint from me about Firefox being slow to start in several months, have you? That's why. Throw enough CPU speed and RAM at a problem and the problem will fade into the background.
Here are some that you might like to consider.
Does Anyone Use a Dictionary These Days?
 Within reach of my right hand, I have The American Heritage Dictionary and Webster's Ninth New Collegiate Dictionary. Within reach of my left hand, there's the Oxford Canadian Dictionary, the Cambridge Dictionary, and the American Heritage Dictionary. I open any one of these books rarely and some of them haven't been touched in years.
Within reach of my right hand, I have The American Heritage Dictionary and Webster's Ninth New Collegiate Dictionary. Within reach of my left hand, there's the Oxford Canadian Dictionary, the Cambridge Dictionary, and the American Heritage Dictionary. I open any one of these books rarely and some of them haven't been touched in years.
That's because most of the time what I need can be found by a quick trip to onelook.com or by using Google's define:word function. Until a year or so ago, I had a CD-based dictionary installed, but I decided that's no longer essential.
Now you can add a dictionary to the search function in Firefox that gives you access to Merriam-Webster Online. [Note: You'll find a lot of cheap Webster dictionaries, but these are invariably substandard works. "Webster" no longer has any real meaning. The real thing carries the name Merriam-Webster.]
Right to Click
 As much as I like Barbara and David Mikkelson's snopes.com website, some recent changes have made it impossible to select text from the site. The Mikkelsons probably prefer that those who cite the site provide a link rather than copying the text, but sometimes I want to cite their research (with attribution) in an article I'm writing. The solution has always been to reveal the page source and copy from there. The problem with this is that the resulting text contains a lot of HTML coding that needs to be removed.
As much as I like Barbara and David Mikkelson's snopes.com website, some recent changes have made it impossible to select text from the site. The Mikkelsons probably prefer that those who cite the site provide a link rather than copying the text, but sometimes I want to cite their research (with attribution) in an article I'm writing. The solution has always been to reveal the page source and copy from there. The problem with this is that the resulting text contains a lot of HTML coding that needs to be removed.
The Right to Click add-on overrides the site's Javascript and makes it possible to select the underlying text.
If you copy something to quote it, remember to give attribution.
Reveal Your Password
 By default, when you type text in a password element, the text is replaced by bullet characters (••••••••). This is fine if someone is looking over your shoulder, but that's not the case most of the time. If you type "psddwird" instead of "password", you'll be refused entry. Wouldn't it be nice to be able to see what you're typing in a password field?
By default, when you type text in a password element, the text is replaced by bullet characters (••••••••). This is fine if someone is looking over your shoulder, but that's not the case most of the time. If you type "psddwird" instead of "password", you'll be refused entry. Wouldn't it be nice to be able to see what you're typing in a password field?
You can. Just download Unhide Passwords and install the add-on. Instead of seeing bullets, you'll see (in faint type) your password.
I use YourMailingListProvider to create the weekly TechByter Worldwide newsletter. When I log on, I can see my password and this eliminates situations in which I commit a typo and find that my login has been rejected. This is also a useful feature when you're signing up for a site and you're required to enter the same password twice.
Being able to see what you're doing is helpful and the fact that the add-on makes the visible password faint still keeps shoulder surfers from causing trouble.
Fake Antivirus Warnings are a Major Threat
I've mentioned these before. You're using a browser and without warning an alert pops up. It suggests that your computer is infected and encourages you to click a link to fix the problem. Chances are, your computer wasn't infected, but if you click the link it probably will be.
Google has conducted a year-long research project that concludes this is a significant threat. (Wow! I could have told you this without a year-long research project.) The thieves who run the operations that create fake pop-up warnings are interested in getting their hands on your money and not in repairing any problems with your computer.
 Google says that the spread of fake antivirus products takes advantage of users’ fear that their computer is vulnerable, as well as their desire to take the proper corrective action. Visiting a malicious or compromised website—or sometimes even viewing a malicious ad—can produce an authentic-looking screen that warns of dire consequences if you ignore it.
Google says that the spread of fake antivirus products takes advantage of users’ fear that their computer is vulnerable, as well as their desire to take the proper corrective action. Visiting a malicious or compromised website—or sometimes even viewing a malicious ad—can produce an authentic-looking screen that warns of dire consequences if you ignore it.
Google recommends running only antivirus and antispyware products "from trusted companies". Google also says that you should "be sure to use the latest versions of this software, and if the scan detects any suspicious programs or applications, remove them immediately."
My recommendation adds this: If you encounter a pop-up message that warns of an infection while using a browser, shut the system down immediately. Click nothing. When you restart the computer, run your existing antivirus program to search for rogue files.
The most important point above is to click nothing. Even clicking what appears to be a Close option can give the application permission to install malware.
The Camera Never Lies, or Does It?
Even in the old days, "the camera never lies" was wrong. By choosing the right lens and an appropriate vantage point, it was easy to distort reality. The soviets were well known for photo compositions that removed "disgraced" leaders from their positions on Lenin's Tomb for May Day Parades. (Lavrentiy Beria there one year, gone the next, for example.) But if you wanted to lie with a camera, you needed some knowledge of optics and the ability to use an airbrush. Today, it's easier.
 Remember the picture of John Kerry and Jane Fonda at a peace rally during the Vietnam war? Great exposé, except for one thing: The image was fabricated. (Details are here.)
Remember the picture of John Kerry and Jane Fonda at a peace rally during the Vietnam war? Great exposé, except for one thing: The image was fabricated. (Details are here.)
UC Berkeley professor of journalism ethics Ken Light photographed Kerry at an anti-war rally in Mineola, New York, in 1971 as Kerry was preparing to give a speech at the rally. Fonda? She didn't attend that particular event. The fake photo was circulated with an Associated Press attribution and many people still think the image is realistic.
Now a University of Albany computer science professor has received a National Science Foundation grant for his project to develop tools that might help detect fakes such as this.
 Computer Science Professor Siwei Lyu received a five-year, $500,000, award that recognizes his accomplishments and potential based on a project titled "A New Statistical Framework for Natural Images with Applications in Vision". Lyu examines a mathematics-based language to describe images and build models to more effectively capture the statistical properties of natural images and to identify fakes.
Computer Science Professor Siwei Lyu received a five-year, $500,000, award that recognizes his accomplishments and potential based on a project titled "A New Statistical Framework for Natural Images with Applications in Vision". Lyu examines a mathematics-based language to describe images and build models to more effectively capture the statistical properties of natural images and to identify fakes.
Lies Are Lies
Opinion: I'm delighted to see a project of this type. It's easy, and becoming easier, for anyone who has access to an application such as Photoshop to make realistic images that have no basis in reality.
University of Albany President George M. Philip refers to Lyu’s award as a deserved recognition of his leading-edge contributions.
The project studies natural image statistics and their applications in fields such as computational neuroscience, image processing, computer vision, and graphics. Lyu says that the project is "based on a simple nonlinear transform that is statistically justified and biologically inspired that provides a new language to describe image signals and forms the basis to build statistical models to more effectively capture statistical properties of natural image." Simple to him, perhaps. This is more like magic to me because digital duplicity can be extremely difficult to spot.
The project attempts to apply "natural image statistics" to the forensic analysis of digital images. Professor Lyu says this will facilitate forensic practitioners in criminal investigations and contributes to national security and public safety.
One important part of Professor Lyu’s project is to develop tools to detect doctored images and to expose image forgeries that have become increasingly prevalent. These doctored images challenge the status of photographs as definitive records of events, especially when images are presented as documentary or legal evidence.
Professor Lyu has been involved in several research projects related to forensic authentication and analysis of digital images. One aim of the current project is to identify images that have been tampered with. Lyu will pursue collaborations with forensic investigators at the New York State Police Department Forensic Investigation Unit to apply some of the techniques in digital image forensics to practical criminal investigations.
In short, this is a project that deserves to be pursued.
Short Circuits
Scratching HP's Palm
Rumored for many days, the deal between HP and Palm was announced this week. The computer giant plans to purchase the fading smartphone provider for approximately $1.2 billion. HP sees value in some of Palm's technology—both hardware and the Palm WebOS operating system—for use in devices that will compete with Apple's Ipad.
HP says the combination will enhance its ability to participate more aggressively in the "fast-growing, highly profitable smartphone and connected mobile device markets." (Next time you buy a phone, remember that "highly profitable" part when you hand over your credit card.) Palm’s operating system will allow HP to sell portable devices that can multitask so that various applications stay up to date.
Under the terms of the merger agreement, Palm stockholders will receive $5.70 in cash for each share of Palm common stock when the deal closes. The transaction is expected to close during HP’s third fiscal quarter, which ends on July 31.
Storming Back
Remember the Storm worm? Perhaps you thought it was gone. Not so. Computer Associates (now known as CA) says that the worm is back although in this iteration it seems not to be particularly widespread (yet) or dangerous (yet).
The worm comes to you as part of a Trojan downloader with Win32/FakeAV or rogue antivirus malware. It does send out a lot of spam, though, which is probably how the user is monetizing the "service". The spams generally deal with adult "dating" sites and online "pharmacies".
CA's Ricardo Robielos performed the research and says that this variant communicates to the spambot server via an HTTP POST command. The server then sends the worm the information to be included in the spams and the infected computer starts sending it to any address it can find on the computer.
Storm was responsible for creating a huge botnet starting in 2007 but was largely eliminated when the primary command and control site was shut down. Additionally, Microsoft's Malicious Software Removal tool cleared the air on more than a quarter million PCs.
Additional information from CA is here.
How to Obtain Fast Internet Connections: Move to Asia
If you don't want to move to Asia to obtain the best Internet access speeds, then try Berkeley, California; Stanford, California; or Chapel Hill, North Carolina. Those are the 3 US cities with the fastest speeds according to acceleration specialist Akami in a report issued this week. Japan leads the rest of the world.
Of the 100 cities with the best speeds, 48 are in Japan and another 14 are in Asia. In the US, 31 states increased their overall Internet speeds in the final quarter of 2009. South Dakota's gain was the greatest (18%) but only to 4.5Mbps. The District of Columbia and 19 other states saw overall rates drop. The sharpest drop was in Virginia, but Akami says that might be because of increased mobile Internet connections. Mobile connections are slower than than wired connections, so that could draw down the average.
Akami monitors nearly 500 million IP connections, about 40% of those in the US and China.
On a country-by-country basis, the best Internet speeds are in South Korea, Hong Kong (even though it's part of China, it is still enumerated as a country) and Japan. All exceeded 7.5Mbps as the average speed! These are also countries with dense populations in cities, which makes creating the infrastructure easier than in places like Montana or North Dakota.
A Final Word: The Internet in a Time of Grief
Last week's program was brief and without a podcast because one of our cats was ill. I had been distracted by that most of the week and a final diagnosis on Saturday required a 5-hour stay at MedVet. During that horrible week, I found the Internet to be useful in dealing with the immediate medical problem and with the grief.
If you have never owned a pet, it may be difficult to understand how much like family members pets are. It was particularly so with Tangerine, who tricked my wife and younger daughter into bringing him home so that he could adopt me. I have owned many cats, but they all stayed with me because I fed and housed them. Tangerine was different. He was a constant companion for reasons of his own.
When it became clear that he had some sort of medical problem on Sunday, I did some research on the Internet. The research was unsuccessful, but it was clear that he needed quick attention, so I called The Cat Doctor on Monday morning and my wife took him in.
The initial diagnosis was grim, but an additional test was recommended and that couldn't be done until Saturday. During the week, I used e-mail and Facebook to communicate with friends. Fearing the best, I began writing a eulogy of sorts, mainly as something to focus my attention on and to keep my head from exploding.
The result of the Saturday tests was a definitive (terrible) diagnosis and again I turned to the Internet to perform some research. Tangerine is no more.
My point is that in a time of crisis, some of the Internet's resources can be called on to provide information and, sometimes, solace.
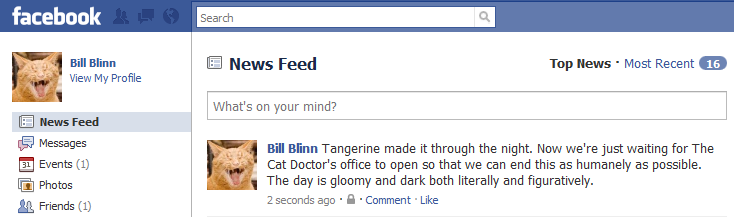
If you would like to read more about Tangerine, his story is here. One correspondent suggested that those of us who enjoy cats, if we are lucky, will find one THE CAT during our lifetimes, a cat that transcends the barrier between species. For me, Tangerine was definitely that singular THE CAT.
Over the years, I've been associated with a lot of cats and, when they've died, I missed them. Occasionally there was one that left me with a deeper sense of sadness. But Tangerine's death left me with a profound sense of loss simply because the relationship between cat and person was significantly different than the usual person-cat relationship. So, farewell my friend. You will be missed.
You will also be remembered vividly for a long, long time.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
