Security: Protecting Your Computer from Malware
The malware threat continues to worsen. As the bad guys become more devious and daring, the good guys work to create resources to avoid, identify, and eliminate malware. Practicing "safe computing" is crucial because you can't depend on software to protect you but some applications can help. This week, and for the next 2 weeks, I'll look at some of the applications you can use to help in the battle to keep your computer safe.
This week's topic is avoidance. Next week we'll consider how to identify security threats and the third week's topic will be malware removal.
Let's start by defining "malware": Malware, short for malicious software, is software designed to infiltrate a computer system without the owner's informed consent. The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware, including true viruses. Software is considered malware based on the perceived intent of the creator rather than any particular features. Malware includes computer viruses, worms, trojan horses, most root kits, spyware, dishonest adware, crimeware, and other malicious and unwanted software. (Source: Wikipedia)
In other words, it's software that you don't want on your computer.
Avoiding the Threat
Avoidance is better than repair for several reasons. Cleaning an infected computer takes time and maybe a lot of it; depending on what malware was installed, your personal information may have been exposed.
There is no one-size-fits-all application that will protect against everything.
You undoubtedly have an antivirus application. Many antivirus providers have expanded their applications to include additional security measures. Although e-mail continues to be a primary vector for malware, the Web is increasingly the fraudsters' choice because many of us continue to use outdated and vulnerable browsers. This is the computer equivalent of driving a car that has no functional brakes.
When I researched the current crop of free and paid protective applications near the end of 2009, I surprised myself by selecting Norton Internet Security 2010. (Read the complete explanation here.)
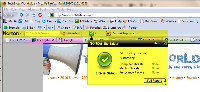 NIS 2010 includes a toolbar that installs into Internet Explorer and Mozilla Firefox. If you try to follow a link that's known to be unsafe, the application will display a warning and provide additional information about the potential threat. When you're on a site, NIS summarizes the site with regard to computer threats, identity-theft threats, and general annoyances.
NIS 2010 includes a toolbar that installs into Internet Explorer and Mozilla Firefox. If you try to follow a link that's known to be unsafe, the application will display a warning and provide additional information about the potential threat. When you're on a site, NIS summarizes the site with regard to computer threats, identity-theft threats, and general annoyances.
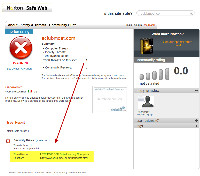 The Full Report button leads to the specifics. Here's an example of a site in Italy that attempts to run an application that disguises itself as "Windows Update" to install malware. You can ignore the warnings and you can even disable this function. Ignoring the warning would be OK if you're certain that the site you're visiting is safe, but I see no reason to disable Norton Safe Web. It's all too easy to make a mistake when you're tired, distracted, or in a hurry.
The Full Report button leads to the specifics. Here's an example of a site in Italy that attempts to run an application that disguises itself as "Windows Update" to install malware. You can ignore the warnings and you can even disable this function. Ignoring the warning would be OK if you're certain that the site you're visiting is safe, but I see no reason to disable Norton Safe Web. It's all too easy to make a mistake when you're tired, distracted, or in a hurry.
Your antivirus program should also contain protection against root kits. A root kit is an example of good software gone bad. Originally used to gain control of an unresponsive system, now root kits are used as malware to give intruders secret access to systems. Root kits are particularly dangerous because they are designed to be invisible. Attackers usually replace a critical system file by tricking a user into running an application ("Trojan horse") that makes the switch.
Updates are important, too. If you're old enough, you may remember quarterly or annual antivirus update disks that arrived by mail. Then the updates were delivered online ever month, or every week, or every day. Norton Internet Security checks for updates every few minutes and downloads new updates many times per day.
Antivirus applications sometimes include a firewall. Users of Windows XP or earlier systems should activate that firewall or some other third-party firewall. Vista and Windows 7 both have adequate firewalls, but previous versions of Windows had a substandard firewall or none at all. If you choose to run the antivirus application's firewall under Vista or Windows 7, the operating system will disable the Windows firewall.
Test Your Firewall
 To test your computer's firewall, visit the Gibson Research Center's Shields Up page and run the tests you find there. If the computer doesn't pass all of the tests, there's a problem with the firewall. Ideally, when you run the full port scan, all ports should be listed in full stealth mode.
To test your computer's firewall, visit the Gibson Research Center's Shields Up page and run the tests you find there. If the computer doesn't pass all of the tests, there's a problem with the firewall. Ideally, when you run the full port scan, all ports should be listed in full stealth mode.
The application should include network monitoring if you have a LAN at home, and particularly if part of the LAN is wireless. It may include parental controls that restrict browsing or Internet access. This is a good way to come to the realization that your children are smarter than you are when it comes to outsmarting software that's intended to "protect" them.
Whether you choose the Norton product or some other vendor's product, be sure to walk through the configuration screens so that you'll understand what the application is doing and why.
Establishing a Baseline
Malware is sneaky, but it's often fairly easy to identify. If it's running on your computer, it should show up in a list of running processes.
So this week I'll show you a way to identify the normal processes. Once you've done this, you'll then be able to identify new processes and this information will help you determine whether the process is good or bad.
You need to know which processes are OK and should be running; the Microsoft Process Explorer creates a baseline report on a clean machine. You can then run the MPE occasionally to identify new processes.
When you find a new process, don't assume that it's bad. It might just be a process that has been spawned by a new (or old) application that you installed. Use a search engine to investigate the name of the process. (More on that in a moment.)
The Microsoft Process Explorer is from SysInternals, a company that Microsoft acquired from Bryce Cogswell and Mark Russinovich in 2006.
No installation required; just unpack the zip file and run it.
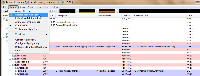 The Process Explorer is a complex tool and it can do significant harm to your computer if misused, but it is the best tool available when it comes to creating a baseline summary of applications. You can expect a full report on the Process Explorer later.
The Process Explorer is a complex tool and it can do significant harm to your computer if misused, but it is the best tool available when it comes to creating a baseline summary of applications. You can expect a full report on the Process Explorer later.
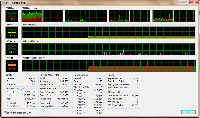 You can replace the basic Task Manager with Process Explorer and I recommend doing this because the Process Explorer does everything the Task Manager can do and more.
You can replace the basic Task Manager with Process Explorer and I recommend doing this because the Process Explorer does everything the Task Manager can do and more.
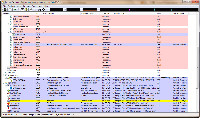 Creating the baseline file is easy. Run Process Explorer, hide the lower pane if it's showing, and then save a copy of the file it offers to create. This file will contain the contents of the Process pane as a tab-delimited text file that can be opened in any spreadsheet program. If you suspect a malware infection, it's easy to compare the baseline file with a new file.
Creating the baseline file is easy. Run Process Explorer, hide the lower pane if it's showing, and then save a copy of the file it offers to create. This file will contain the contents of the Process pane as a tab-delimited text file that can be opened in any spreadsheet program. If you suspect a malware infection, it's easy to compare the baseline file with a new file.
This doesn't provide a definitive answer! Processes can come and go for legitimate reasons, so it's important to avoid the temptation to delete the file responsible for what appears to be a new process. Doing so might make the problem worse. But if you need a technician to take a look at your computer, this is the kind of information the technician will find helpful.
Before taking any action, perform a Google search on the process name. Or use the even faster method: Visit Uniblue's Process Library to learn more about the file.
Next week, I'll help you establish a system baseline that will help you find malware infections.
OpenDNS is Better than Your ISP's DNS
This is one of those techie accounts that might scare non-techies away. But it shouldn't because it's really not very complicated even though it sounds intimidating. Stick with me for a moment and maybe I'll convince you that you should change your DNS server and that you can. DNS is an initialism for "domain name service". The DNS server is responsible for converting a name that makes sense to you (microsoft.com) to something that computers can use (65.55.12.249). Your Internet service provider converts "microsoft.com" to "65.55.12.249" (or, more accurately, to 01000001, 00110111, 00001100, 11111001). If your ISP already does this, why whould you want to use some other service? I can explain. Maybe.
Let's start with Wikipedia: "The Domain Name System (DNS) is a hierarchical naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participants. Most importantly, it translates domain names meaningful to humans into the numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide. An often used analogy to explain the Domain Name System is that it serves as the 'phone book' for the Internet by translating human-friendly computer host names into IP addresses. For example, www.example.com translates to 208.77.188.166."
"Phone book" is the key concept. You type a name that you can remember. The DNS server looks up that name and uses the associated number to make the connection. Because of this, you don't need to remember a series of cryptic numbers.
Back to Wikipedia: "The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. Authoritative name servers are assigned to be responsible for their particular domains, and in turn can assign other authoritative name servers for their sub-domains. This mechanism has made the DNS distributed, fault tolerant, and helped avoid the need for a single central register to be continually consulted and updated."
So why would you want to use a 3rd-party DNS service instead of the one provided by your ISP? And why might you want to pay $10 per year for a service you can receive for free?
Your ISP probably won't protect you from the creeps who try to con you into providing information about your bank or credit card and OpenDNS will. The free OpenDNS service can warn you if you accidentally click a dangerous link. If someone tries to send you to a known phishing website, OpenDNS blocks the site and tells you about the site's malicious intent.
But that's not all. OpenDNS is probably faster and more accurate than the DNS your ISP provides. OpenDNS has a global network of servers with software that routes DNS requests to the OpenDNS server that's physically closest to you.
There's no reason not to do this.
Why OpenDNS is Better
Your ISP's DNS will connect you to the right IP address if you spell the domain name right and that's about it. OpenDNS will do that, too, but it includes several valuable (free) features.
OpenDNS has your back: OpenDNS identifies known phishing sites and alerts you if you try to visit one. You can still go to the site if you wish, but at least you'll have been warned.
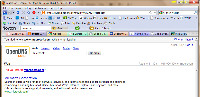 Address corrections: Type an incorrect URL (mucrosoft.com, for example) and OpenDNS will suggest that maybe you're looking for microsoft.com if the domain you requested isn't active.
Address corrections: Type an incorrect URL (mucrosoft.com, for example) and OpenDNS will suggest that maybe you're looking for microsoft.com if the domain you requested isn't active.
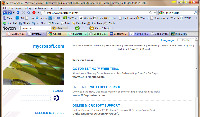 If the domain is active, though, all OpenDNS can do is take you there. Here's an example with "mycrosoft.com". The name is owned by what's called a "typo squatter" and legitimate (!) businesses pay to have their ads placed on these sites. If you find yourself on a typo squatter's site, my recommendation is that you click no links.
If the domain is active, though, all OpenDNS can do is take you there. Here's an example with "mycrosoft.com". The name is owned by what's called a "typo squatter" and legitimate (!) businesses pay to have their ads placed on these sites. If you find yourself on a typo squatter's site, my recommendation is that you click no links.
Typo squatting isn't illegal, but it's not something that I consider ethical.- Customize the experience: Add an image of your choosing and a personalized message to the OpenDNS Guide for pages that do not exist or are blocked. If you're using the service's parental controls, this might impress your children.
The OpenDNS Guide offers suggestions when you mistype a URL or try to visit a site that's down. In other words, it replaces cryptic 404-error pages. 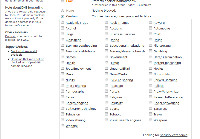 Watching out for your family: OpenDNS gives you more than 50 filtering categories to choose from. Simply check the boxes of the categories you want to block and the filtering goes into effect in minutes.
Watching out for your family: OpenDNS gives you more than 50 filtering categories to choose from. Simply check the boxes of the categories you want to block and the filtering goes into effect in minutes.
As with any service of this sort, caution is recommended because the blocks can have unintended consequences. If you select "Weapons", you children may have trouble searching for information about World War II and if you select "Pornography", some scientific sites that deal with genetics or sexuality might be blocked.
Free or Paid?
If you're interested in giving your family access only to sites you have approved, the paid version is what you need. If you trust your spouse and children, maybe all you need is the free version.
The free version will route you to a "search" page if you type a domain name that doesn't exist. That's how the company monetizes its service. The primary advantage is that the search page is a legitimate site, not the site you might find if your ISP's DNS server couldn't find the page.
Setting Up OpenDNS
 How you set up OpenDNS depends on whether you have a router or not.
How you set up OpenDNS depends on whether you have a router or not.
- If you have a router, you'll need to log on to it and change the DNS setting from the default (obtain from the ISP) to the two OpenDNS IP addresses. Complete instructions are provided for a multitude of router brands on the OpenDNS website.
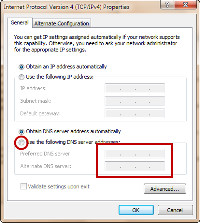 If you don't have a router, you'll need to configure your computer's network settings. OpenDNS provides instructions for Windows (XP, Vista, 2000, NT, 98, Windows 7, ME), Mac (OS 9 and OS X), Linux (SUSE and Ubuntu), and Other (Wii).
If you don't have a router, you'll need to configure your computer's network settings. OpenDNS provides instructions for Windows (XP, Vista, 2000, NT, 98, Windows 7, ME), Mac (OS 9 and OS X), Linux (SUSE and Ubuntu), and Other (Wii).
If you can use the service for free, why might you want to pay for it? Your choices are $10 per year or "starting at $2000 per year". The high price is for enterprise users. Free and $10 are for home and small-office users.
 The paid version increases the number of domains that can be whitelisted or blacklisted from 25 to 50 and offers better support. In addition, you can limit the sites your family can visit to just the sites you specify. You already know that I'm not a fan of this approach. There's nothing on the Internet that your children won't see on their own in the outside world. You can help them place things in context. But if this is the approach you want to take, you won't find a better system or a lower price.
The paid version increases the number of domains that can be whitelisted or blacklisted from 25 to 50 and offers better support. In addition, you can limit the sites your family can visit to just the sites you specify. You already know that I'm not a fan of this approach. There's nothing on the Internet that your children won't see on their own in the outside world. You can help them place things in context. But if this is the approach you want to take, you won't find a better system or a lower price.
 Bottom Line: DNS that's better than what your ISP offers.
Bottom Line: DNS that's better than what your ISP offers.
The ability to block phishing sites alone is worth the small effort required to set up OpenDNS. Add to that the other features the service provides and the fact that it's probably faster than your ISP's DNS makes this a decision that requires no thought at all.
For more information, visit the OpenDNS website.
The Other "God Mode" GUIDs
In early January, I wrote about the "God Mode" under Windows 7. It involves creating a directory that can be named anything (instead of "God Mode", I named mine "Devil's Playground"). The special directory makes a huge list of Windows functions available. At the same time, I reported that Ina Fried at Cnet News had a list of other special directories. She didn't know what they were and neither did I. Now I do.
The God Mode directory needs to be named
Something.{ED7BA470-8E54-465E-825C-99712043E01C}
where "Something" can be anything at all. The dot, curly braces, and GUID must be exactly as shown. GUID, as you'll recall, is a "globally unique identifier" and the term is usually used in reference to Microsoft's Universally Unique Identifier (UUID) standard that was developed for Windows. You'll find GUIDs scattered all through the Registry.
Now I've installed the other God Mode directories and here's what they are:
- {00C6D95F-329C-409a-81D7-C46C66EA7F33} Location
- {0142e4d0-fb7a-11dc-ba4a-000ffe7ab428} Biometric devices
- {025A5937-A6BE-4686-A844-36FE4BEC8B6D} Power
- {05d7b0f4-2121-4eff-bf6b-ed3f69b894d9} Task Bar
- {1206F5F1-0569-412C-8FEC-3204630DFB70} Logon Credentials
- {15eae92e-f17a-4431-9f28-805e482dafd4} Install Program from Network
- {17cd9488-1228-4b2f-88ce-4298e93e0966} Default Apps
- {1D2680C9-0E2A-469d-B787-065558BC7D43} Public Keys
- {1FA9085F-25A2-489B-85D4-86326EEDCD87} Wireless Networks
- {208D2C60-3AEA-1069-A2D7-08002B30309D} Network (WORKGROUP)
- {20D04FE0-3AEA-1069-A2D8-08002B30309D} Disk Drives
- {2227A280-3AEA-1069-A2DE-08002B30309D} Printers
- {241D7C96-F8BF-4F85-B01F-E2B043341A4B} Remote Desktop
- {4026492F-2F69-46B8-B9BF-5654FC07E423} Windows Firewall
- {62D8ED13-C9D0-4CE8-A914-47DD628FB1B0} Unknown/Non-functional in Win7/64
- {78F3955E-3B90-4184-BD14-5397C15F1EFC} Performance
Keep in mind that these don't work in Windows XP. Some of them will work in Windows Vista. All should work in Windows 7/32. I thought that all would work in Windows 7/64, but one didn't.
What's the point? Probably there isn't much of a point. The original God Mode makes a lot of functions easily accessible. The others aren't particularly useful; all of them simply make available functions that you can find quickly in the Control Panel.
But at least now I know.
Short Circuits
I Own A Multi-Million-Dollar Computer
The cost of solid-state memory and disk space has dropped so fast over the past few years that it's nearly impossible to comprehend. If somebody had told me, in 1985, that I would one day own a computer with 8GB of solid-state memory (RAM) I would have thought that person to be a fool. I had just paid several hundred dollars to increase the RAM in my first computer from 256KB to 320KB.
In those days, memory cost nearly $1000 per megabyte. By the end of the year, the price would drop to about $300 per megabyte, but at those prices a gigabyte of memory would cost $30,000 and 8GB would go for $240,000. In the mid 80s, a computer with a lot of memory had 1MB of RAM.
I would have been skeptical even in the mid 1990s. Memory cost around $30 per MB then, but 8GB would have cost $24,000 and I simply wouldn't have been able to visualize a personal computer with that much memory.
Today RAM costs less than 5 cents per megabyte, so I found that I could entertain the thought of 8GB of memory. I continue to say this about memory: If you want a faster computer, the most cost-effective way of achieving your goal is to add as much memory as the system can use.
Oh ... And if that same person had told me, in 1985, that I would own a computer with nearly 4 terabytes of disk storage, I would have thought him to be a lunatic. But now I do and it's on my desktop.
Times change, I guess.
Why I Continue to Like BlueHost
At the bottom of each page of the TechByter website, you'll see a small advertisement for BlueHost.com. You might think that I do this because BlueHost pays me when someone signs up for an account after clicking the link. That's true, but there's another reason: I believe that the company provides excellent service for what it charges. Beyond that, top management is accessible when something goes wrong.
On March 13, I tried to connect to my website to replace a file and my credentials were rejected.
FTP can report rejections, but not the reasons. I thought I'd see if the control panel could tell me anything: When I tried to log on, I was told that I had to change my password. It was a security issue, the message said.
The problem was easy enough to fix, but I wondered why BlueHost hadn't notified me in advance. I wrote to the BlueHost CEO:
Matt,
I received a message from James Grierson earlier this week to let me know that the affiliates program would be strengthening security and that I needed to log on with a new password. The change to secure passwords is good and so is the advance notice.
But today I attempted to connect via FTP and my credentials were rejected. There was no explanation, probably because it would be difficult to set up the FTP server to provide that kind of notification. So why wasn't there an e-mail message to explain the change?
Some users could be really puzzled when they can't get an FTP connection and, unless they go to the control panel and figure it out, they'll probably just open support tickets. That's not good for your customers or your support staff.
Because there was no warning about this, I had budgeted no time to deal with it and I spent a couple of hours that I didn't have updating passwords and then updating password files on 3 computers. Improving security is a good thing, but the implementation certainly could have been better.
Bear in mind that BlueHost is an organization that hosts hundreds of thousands of websites. The rest of the story is why I continue to recommend BlueHost to friends and clients. A few hours later, BlueHost CEO Matt Heaton, replied:
There was a botnet actively trying to brute force user accounts and some with very weak passwords were being cracked. The velocity of the attack warranted immediate action on our part and any advance notice would have alerted the botnet to quicken its attacks. This is the reason we chose to implement it this way.Top management at BlueHost was certainly involved in the effort to keep the system secure, yet the CEO took time out to let a small customer know what was going on. That's the way things should work, but seldom do.
I completely agree that most times we are very poor when it comes to giving advance notice, but in this instance I hope you can understand the reasoning behind the implementation.
I am very sorry for the inconvenience.
Thanks,
Matt Heaton / Bluehost.com


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
