A Bullet-Proof Multi-Part Backup Plan
Backup is important. I mention that often enough that you're probably sick of reading about it, but it really is important. Often I talk about Carbonite, an online backup service that makes the process so easy that nobody can honestly say it's too difficult to understand. But as much as I like Carbonite, it's not my only backup. I also use Acronis True Image and I think you should, too.
Since I last wrote about this topic, I've added yet another layer of protection. My computer is used for testing and research, for website development, for time billing, and for educational projects. It also contains tens of thousands of digital photographs I've take over the years and tens of thousands of music tracks.
Losing the music would be annoying, but survivable. I can always recreate the tracks from the original CDs. Losing the digital photographs would be much worse. All of our family photographs from about 1998 on exist only in digital format. There are no negatives. In most cases, there are no prints. So losing the digital images would be far more than annoying.
One step beyond that would be websites developed for clients, time billing files, and tax records. To mitigate the dangers, I store most website development files on the website, so recovery wouldn't be too difficult in the event of a catastrophic failure. But I would have to restore files from dozens of websites. Time billing and tax records would be even worse.
A little paranoia is a healthy thing when it comes to backup, so my current backup strategy consists of the following:
- Carbonite backs up most of my data files and is updated as close to real time as possible.
- Acronis True Image backs up the system files and the most critical data files and is updated weekly.
- Websites are backed up on both of the above and in a private directory on the website.
- Websites and the other most critical files are backed up on a "hot backup" drive, a USB drive that's attached to the primary computer. This drive can be attached to my notebook computer to allow business continuity in the event of a system failure.
- (NEW) The most critical files are also backed up to a local drive that's inside the primary computer.
Any backup device that is in the same physical location as the device it's being used to back up cannot be considered to be a workable backup device. That's because a fire or thief that destroys or steals the primary system will probably also get the backup system. That's why an off-site, online backup is important. And it's why an off-site disk-based backup is important.
What Can Go Wrong?
Anything and everything can go wrong.
- If I accidentally delete or damage a file, I can probably restore it from the internal backup or the external hot backup. If not, and it has been changed recently, I can use Carbonite. If it hasn't been changed within the past week, I can get it from Acronis.
- In the event of a fire or other major problem, I can restore files from the Acronis backup or the Carbonite backup. Acronis would be faster if I need to recover the entire disk drive; Carbonite would be faster if I need to recover just a few files.
- To lose a truly critical file that I've created for a client, the following would need to occur:
- Primary computer system (Worthington, Ohio) is damaged or destroyed. If this happens, both my internal backup and my external hot backup will also be unavailable.
- Web server (Orem, Utah) is damaged or destroyed.
- Carbonite server (Boston, Massachusetts) is damaged or destroyed.
- External off-site backup (Hilliard, Ohio) is damaged or destroyed.
The above case is the most serious case I can imagine: Simultaneous loss of facilities in Worthington, Boston, Orem, and Hilliard. Should that happen, I suspect that data retention will be about number 257 on my list of critical concerns.
You can't protect against everything, but you can take reasonable precautions without needing to spend a lot of money.
The Cost of a Good Backup Plan
It may be less than you think.
- For $50 to $100, you can add an additional 500-1000MB drive in your computer.
- For $100 to $150, you can add an external USB hard drive.
- For $50 per year, you can add Carbonite backup.
- For $50, you can add Acronis True Image Home and another $50 to $100 will include an external hard drive that you can store at the office or in a safe-deposit box at your bank.
You don't need to add all of these options to your computer, but adding just one or two will make recovery easy.
Tune Up: A Buggy But Useful Itunes Helper
From the name, you might think Tune Up would make your computer run better. It doesn't, but it makes Itunes look a lot better. A lot of my tracks in Itunes are from CDs or records that I own. As a result, they didn't have cover art and sometimes the track information and other metadata were wrong. I could use Itunes to obtain the cover art and manually edit the track names and add the metadata, but there's a much better way.
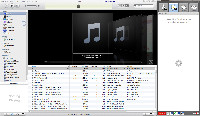 TuneUp works with Itunes. When you drag selections to the clean-up panel (TuneUp recommends no more than about 500 at a time, but it will take more if you don't mind the occasional application crash). Maybe Cover Flow looks like this -- lots of gray covers with music notes on them. Ugh.
TuneUp works with Itunes. When you drag selections to the clean-up panel (TuneUp recommends no more than about 500 at a time, but it will take more if you don't mind the occasional application crash). Maybe Cover Flow looks like this -- lots of gray covers with music notes on them. Ugh.
It's easy to drag selections to TuneUp because it sits at the right side of Itunes and you can set it to start automatically when Itunes does. I had to turn that off because I'm using Windows 7 on a 64-bit system. TuneUp isn't yet fully certified for Windows 7, but it works OK most of the time; I just found that starting it with Itunes caused problems, so I docked the TuneUp icon on the Task Bar next to the Itunes icon.
 And the crashing I mentioned isn't terribly serious, just a bit annoying. If TuneUp stops working, you'll need to use the Task Manager to kill it, but anything it's already done will have been retained.
And the crashing I mentioned isn't terribly serious, just a bit annoying. If TuneUp stops working, you'll need to use the Task Manager to kill it, but anything it's already done will have been retained.
TuneUp's "Clean" process "takes an acoustic fingerprint of each song and references it against a robust database of more than 90 million indexed tracks," the developer says. And because TuneUp does this, it will usually come back with the right information regardless of how bad the original metadata is.
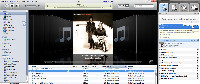 The returned information is sorted into 2 categories: Ones that TuneUp believes absolutely to be correct and ones that TuneUp is reasonably certain are correct. You have the option to view every track in each set and to keep or reject any of the program's suggestions. Maybe there's a third category: Ones that TuneUp couldn't find. You won't see a lot of those.
The returned information is sorted into 2 categories: Ones that TuneUp believes absolutely to be correct and ones that TuneUp is reasonably certain are correct. You have the option to view every track in each set and to keep or reject any of the program's suggestions. Maybe there's a third category: Ones that TuneUp couldn't find. You won't see a lot of those.
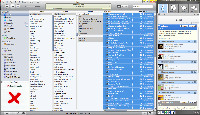 Besides providing all the missing metadata, this process also retrieves cover art in most cases. Sometimes it can't find anything or the image it finds is in a format that TuneUp can't deal with. But my collection went from about 2% with cover art to about 70%. That may seem a bit low but the vast majority of the tunes in the 30% without cover art simply don't have any cover art because they're not from commercial CDs. A lot of them are old radio programs, so TuneUp actually retrieved artwork for more than 90% of the tracks that have cover art.
Besides providing all the missing metadata, this process also retrieves cover art in most cases. Sometimes it can't find anything or the image it finds is in a format that TuneUp can't deal with. But my collection went from about 2% with cover art to about 70%. That may seem a bit low but the vast majority of the tunes in the 30% without cover art simply don't have any cover art because they're not from commercial CDs. A lot of them are old radio programs, so TuneUp actually retrieved artwork for more than 90% of the tracks that have cover art.
In addition, there's an option to retrieve just cover art. You could use this if the metadata is good and the only problem is missing covers.
TuneUp has 2 more tabs that come into play when you're listening to music: Tuniverse and Concerts.
Tuniverse can help lead you to music from artists similar to the artists you already like, music that's in some way related to the track you're currently listening to. You'll also see additional music-related content from the Internet, based on what's playing. In addition, you'll find links to music videos and information about the artists.
Tell the Concerts tab where you live and it will display all the concerts it knows about. Find one you like and TuneUp will allow you to buy tickets online.
There are lots of ways that TuneUpMedia can monetize its service, so you might think the application is free. It's not. You can use it to clean 50 tunes or retrieve 100 cover images, but then you have to buy it: $20 for a 1-year license or $30 for a "lifetime" license. That's the lifetime of the computer, by the way; not your lifetime. If you're looking just to clean up an existing mess the 1-year license might be enough. You can continue to use TuneUp for Tuniverse and Concerts without a license.
Although the operation of TuneUp has been hampered by various problems, most probably stemming from my use of Windows 7, I've found TuneUp support to be reasonably quick to respond and accurate in providing suggestions.
 Bottom Line: TuneUp does what it promises and cleans up Itunes.
Bottom Line: TuneUp does what it promises and cleans up Itunes.
If you never use the Itunes Cover Flow option because all the covers are gray, this is just what you're looking for. If you have lots of selections that are misnamed or are missing metadata, this is just what you're looking for. And even if you think it should be free, give the free trial a try: You'll probably decide that the time you'll save and the drudgery you'll avoid will be well worth the cost of cleaning up your Itunes collection.
For more information, visit the TuneUp website.
A Link to Avoid
Your e-mail in box contains a message from someone you know. The message has no subject. There's no signature. You notice dozens of other e-mail addresses in the to line. Some of these addresses are familiar to you, but others are not. The message consists of a single line of text, a URL to a website you've never heard of. Would you click it?
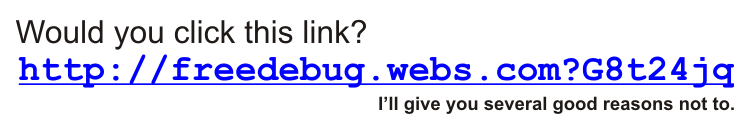
I wouldn't and there are lots of reasons for my reluctance to click.
First, I know that this is a common trick used by people who want to put malicious software on your computer -- applications that can turn your computer into a spambot or collect your keystrokes (bank name, password, etc.) and send them back to the bad guys.
This doesn't mean that you should never click another link, but it does mean that you need to treat each link you see with a certain amount of skepticism.
A link that arrives without any explanation of what it is or why I would be interested in it is not a link I will ever click, even if it claims to come from someone I know.
I also look for consistency. If the message without a signature line has come from someone I know and that person either has a standard signature or always includes some sort of sign-off, a message without a signature won't pass my first security test.
A link to an obscure website or a free hosting service raises concerns.
Any link that includes nonsense letters is a non-starter, too.
I have nothing against link shorteners (tinyurl.com and bit.ly, for example) but a message that includes one needs either a full explanation from the sender or it needs the full URL to be nearby.
A message without a subject is suspicious and, if the message does have a subject line, it needs to sound like something the sender would have written. A message from a writer or editor, for example, shouldn't contain incorrect grammar or spelling errors.
And the message, if there is one, must sound like something the sender wrote. If you've been reading or listening to TechByter for even just a few months, you know how I write. So if someday you receive a message that purports to be from me and it looks like this, you'll know it's not from me: "Hey, doodz! Check out the chicks at this grate pron site!"
Dat ain't me. Don't be fooled. Take no substitutes.
Nigerian Spammers Migrate to Benin
I received a message from Ruben Moussa, Inspector General of Police in Benin, a country in west Africa. Among Benin's neighbor countries is Nigeria, and apparently some Nigerian crooks have decided to move their business to Benin. The inspector general told me that my e-mail address was found in the records of some "scam gangsters" and that this country wanted to make good on my misfortune by issuing me a special ATM card that would be delivered by DHL.
Alarm bells were deafening, but I thought I would briefly suspend disbelief, as if I had gone to a movie or stage play. That turned out to be difficult.
First, "inspector general" Moussa seemed to think that by writing in 24-point bold text he would make his message more convincing. That wasn't exactly the effect that he achieved.
The punctuation and spelling, of course, made the message laughable:
- I was addressed, not by name, but as "Dear valued one".
- The message was sent to "undisclosed recipients".
- The "Ministry of Finance Republic of Benin" held a "cogent (sic) meeting" in January and set aside the paltry sum of $1.5 million USD to "compensate all the concercned (sic) victims."
- A huge amount of money "muts (sic) be delivered" to me only by my consent.
- "However, at the same hand," I am advised to contact the e-mail address shown on the message (a G-mail account!) for further information
I'm certain that nobody who reads or listens to TechByter Worldwide would fall for such an obvious con, but I have to wonder who would. Somebody must; otherwise the crooks would find some other way to make money.
Lessons Crooks Need to Learn for Success
I've mentioned a time or two that the average crook is somewhat unlikely to be the holder of a Phi Beta Kappa key, a member of Mensa, or the class valedictorian. This week I received spam from a spammer who wants me to buy things on my credit card, ship them to him, and wait for reimbursement. When the reimbursement arrives, it will be in the form of a "cashier's check" and the check will be for more than the amount owed. I will be asked to return the "extra". A few days later, the check will prove to be a phony and I will be out not only the cost of the goods I bought for the crook but also the cash I sent.
It's one of the older cons and it's surprising that people still fall for it. Take a look:
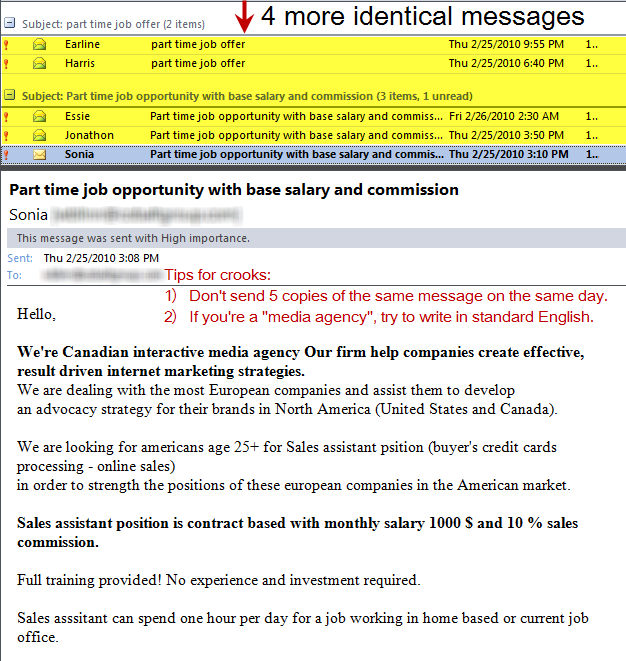
I received 5 copies of the message within minutes of each other. All had someone else's name as the sender, but each had my address as both the sender and the recipient. This is quite easy to do, but it's a dead giveaway. This spam was sent to my office address. At home, I automatically reject all messages that come from "me".
Now let's parse the message itself just for fun.
- We're Canadian interactive media agency Our firm help companies create effective, result driven internet marketing strategies. If you're a media agency, I would expect you to be able to write in decent English, to know you you need either a definite ("the") or indefinite ("a"/"an") article before "Canadian", to understand that sentences should end with some form of punctuation, that result-driven should be hyphenated, and that "Internet" is a proper noun that should be capitalized.
- We are dealing with the most European companies and assist them to develop an advocacy strategy for their brands in North America (United States and Canada). I'm glad to see that they're dealing with the most European companies; I certainly wouldn't want to work with someone who's dealing with just partially European companies. And telling me that North America includes both the United States and Canada is a nice touch.
- We are looking for americans age 25+ for Sales assistant psition (buyer's credit cards processing - online sales (line break) in order to strength the position of these european companies in the American market. Why are americans and european lower case while Sales and American are capitalized? Why did they misspell position? And can anyone tell me exactly what this sentence is attempting to communicate based solely on the words used?
- Sales assistant position is contract based with monthly salary 1000$ and 10% sales commission. Another missing article (a monthly salary) and neither Americans nor Canadians typically place the dollar sign to the right of the amount.
- Full training provided! No experience and investment required. Here's another clear indication that this wasn't written by a native speaker: It should be No experience or investment required.
- Sales assistant can spend one hour per day for a job working in home based or current job office. My guess is that this was written by someone whose first language is one of the Slavic tongues.
Still, the most surprising aspect of this mess is the fact that the spammer sent 5 copies of the same message to one address. This would indicate that the spammer doesn't know how to use the spam application or that the spammer is an utter fool. Or both.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
