|
|||||||||||||||||||||||||||||||
| Previous page | Do you use a pop-up blocker? If so, please read this. | ||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||
| Show Date: 2007.12.09 | |||||||||||||||||||||||||||||||
Ubuntu Linux continues to surpriseIt could easily and successfully be argued that the best time to set up a new operating system and install applications is not on the day when the doctor has prescribed regular doses of post-operative happy pills. Despite the apparent futility of such an exercise, that's exactly what I attempted in mid November following foot surgery. Besides being directed to consume the happy pills every few hours, I was told to sit with my feet elevated. That meant using the desktop computer was out and the notebook computer was loaded with a disk drive that contained Ubuntu Linux. So I sat in an office chair, propped my feet up, and started working on software setup. What happened next surprised even me. To veer off on a tangent immediately, starting with a brief description of Percocet may be helpful. Drugs.com says “Percocet can cause side effects that may impair your thinking or reactions. Be careful if you drive or do anything that requires you to be awake and alert.” Computing under the influence of a schedule 2 controlled substance might be viewed as looking for trouble. But what else was there to do? I had already set up the operating system, which included the Open Office suite and some other applications, and I had installed some additional applications. If I was to be able to use the computer for anything more than solitaire while sitting with my feet elevated, I needed to set up Evolution, the e-mail program that was included with Ubuntu, and configure the other applications. This report started as a stream of consciousness series of notes written in AbiWord. Before you see it, I’ll have attempted to clean it up a bit, organize it, and remove at least some of the typos and other errors. Applications under UbuntuA word processorAlthough I started keeping these notes in AbiWord, I quickly converted them to OpenOffice Writer because it has more features and because it supports typographic quotation marks. AbiWord has been in development for many years and the process is excruciatingly slow. I reviewed the Windows version of the application in 2004, when its primary feature was support for languages that are printed from right to left as well as those that are printed from left to right. It hasn’t progressed much from there. OpenOffice Writer, on the other hand, is much more like Microsoft Word, both in user interface and in features.
Collecting e-mailEvolution is the OpenOffice equivalent of Outlook. It was easy to set up my two primary e-mail accounts and establish sorting rules for the primary sources of mail. Evolution sorting is at least as powerful as that provided by Outlook, but far less powerful than that provided by The Bat. In The Bat, I have dozens of rules that are composed from complex rules that include sets with both Boolean or and Boolean and conditions, sometimes followed by multiple actions. Evolutions filters can look at the sender, the receiver, text in the body of the message or the subject line, specific header information, and more; the primary shortcoming is that you can’t specify complex and/or conditions: All conditions must be met (“and”) or any condition must be met (“or”). As e-mail programs go, the filters are relatively strong; compared to The Bat, they’re nothing. Still, even operating on half-power (or less) because of the Percocet, I had the accounts set up in less than 10 minutes and my most critical filters functioning within half an hour. Then I wanted to import my address book from The Bat. On the desktop, I exported the directory in several formats to a flash drive, then plugged the flash drive in to the notebook. I asked Evolution to import the LDIF file I had created and a few seconds later all of my contacts from The Bat were present. BrowsingDepending on your point of view, you may consider it good or bad that Microsoft’s Internet Explorer isn’t available for Linux. Firefox is installed by default and that’s OK with me because that’s the browser I prefer. Opera isn’t shown in the pre-installed list of available applications, so I had to go look for it. Opera detected Ubuntu version 7.10 and offered a self-installer package. Immediately following the installation, the Ubuntu update procedure let me know that an update was available. Two browsers should be adequate. Setting up a dual boot (not quite yet)I may not go the dual-boot route for a while on the notebook because the DVD player isn’t entirely reliable and I don’t want to risk a failure during the boot loader installation because that would kill the Windows XP installation on the disk. Maybe someday, but definitely not while I’m mentally fuzzy. I know from reading reports by those who have set up Ubuntu to be part of a dual-boot system on a Windows machine that it’s a trivial operation if you make sure that you have a just-in-case full backup and you carefully follow the installation steps. A command-line feature and the the ability to run (some) Windows appsIn the old days, the command line was all there was. The C prompt (or equivalent in other operating systems) was a step up from 80-column cards, paper tape, and printing terminals. But then Xerox, Apple, and Microsoft developed variants of the graphical user interface. Mac users in particular made fun of the DOS underpinnings of Windows. That was before Apple started using Unix as the base for OS X. Unix and Linux have always had a strong command line. Windows Vista has a robust command line. So does OS X and, instead of making fun of the command line, Apple-centric magazines are now embracing it. As a Linux user, you’ll want quick access to the command line and YaKuake provides just that. Once started, YaKuake hides until you press the activation key (F12 by default, but I changed it to Ctrl-Alt-F12 because OpenOffice Writer uses F12). And if you have a Windows-only program that you need, take a look at WINE, which runs some Windows applications without having to install Windows. Some. If you need to run Adobe CS3 applications, WINE is not a good solution; but it’s perfect if you need to run a utility such as PINS, which keeps track of your user IDs and passwords.
Seeking out useful informationSo far, everything I've set up has been surprisingly easy. Most of the Linux distributions are easier to use than in the past. Some friends use Fedora and it has some similar options for managing packages and dependencies so that they're largely transparent to the user. The new user of Linux has a lot of resources. Although I’ve installed several Linux distributions, I haven’t worked with Linux directly for several years. For that reason, I consider myself a new user. I mentioned in an earlier report the Ubuntu discussion lists, but those are mainly ways to find answers to questions. I was seeking more general information—suggestions for getting started. Miscellaneous data points
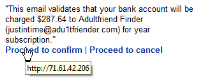
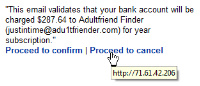
Windows Vista securityWindows XP has only 2 kinds of user account: Administrators (who can do everything) and everybody else (who can do nothing). Because the non-administrator accounts are so limited, everyone gets an administrator account. This is a lot like allowing all Unix/Linux users to run as root. Dumb. Windows Vista adds a layer and provides the oft-maligned user account control (UAC). UAC allows most users to log in as standard users because a standard user who knows the administrator's password can allow potentially unsafe actions to proceed by providing that password. UAC asks for permission before performing actions that could potentially affect the computer's operation or change settings that affect other users. An administrator who sees a UAC message can simply indicate approval; standard users must provide an administrator's password to proceed. The goal of UAC is to prevent malware and spyware being installed. There are 4 categories of UAC messages: Windows needs your permission to continue: A Windows function or program that can affect other users of this computer needs your permission to start. Check the name of the action to ensure that it's a function or program you want to run. A program needs your permission to continue: A program that's not part of Windows needs your permission to start. It has a valid digital signature indicating its name and its publisher, which helps to ensure that the program is what it claims to be. Make sure that this is a program that you intended to run. An unidentified program wants access to your computer: An unidentified program is one that doesn't have a valid digital signature from its publisher to ensure that the program is what it claims to be. This doesn't necessarily indicate danger, as many older, legitimate programs lack signatures. However, you should use extra caution and only allow this program to run if you obtained it from a trusted source, such as the original CD or a publisher's website. This program has been blocked: This is a program that an administrator has specifically blocked from running on your computer. To run this program, you must contact your administrator and ask to have the program unblocked. Microsoft recommends that most users log on with a standard user account most of the time. You can surf the Internet, send e-mail, and use a word processor without an administrator account. When you want to perform an administrative task, such as installing a new program or changing a setting that will affect other users, you don't have to switch to an administrator account. Windows will prompt you for permission or an administrator password before performing the task. To help protect your computer, you can create standard user accounts for all the users who share the computer. When someone who has a standard account tries to install software, Windows will ask for an administrator account's password so that software can't be installed without your knowledge and permission. Stupid spam of the week and one that's not so stupid"JustInTime" wrote to me from "Adu1tFriendFinder" to say that my bank account would be charged $287.64 for a "year subscription". Yes, that's a "1" in place of the letter "l" in the name. And I have enough adult friends, so I probably don't need any more. (Oh, that kind of adult!) Well, I don't need that, either. My two options were Proceed to confirm and Proceed to cancel. Both of the links went to the same location, not too surprisingly it was an IP address instead of a domain name. I didn't visit to see what the site had in store for me, but I did wonder. Later, I received yet another offer from yet another barrister who wanted to make me very rich. The presentation is improving. The IP address is in a range owned by Comcast and, by the time I had an opportunity to use a safe application to see what bad stuff would be loaded onto my computer if I just clicked either of the links, whatever was there had been shut down.
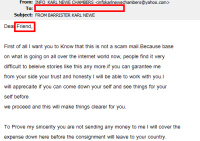
The letter from the "barrister" was a bit more convincing. It was reasonably well written, almost as if the writer actually had some passing experience with the English language. And the letter did what several recent samples I've seen have tried: It admitted that there are a lot of scams such as this and reassures me that I will not need to send any money. (That would come later, of course.) The writer had also discovered that pressing the CAPS LOCK key will turn off that feature and allow messages to be composed in upper and lower case text. That was a refreshing change. But there was no name in the "to" field, which means that the message was blind-copied to more than a single person. The average attorney would be looking for one person and would not send a broadcast e-mail. Further damaging the image, the writer called me "Dear Friend" instead of using my name. And I happen to know that "barristers" don't do this kind of work. They are high-priced chaps who represent you in court. You won't receive an inheritance letter, not even a valid one, from a barrister.
Here's the full text of the message. I leave it up to you to find all of the typing errors, spelling errors, and infelicities that give away the fact that the writer is not a native speaker of English.
Nerdly NewsA slap in the old FacebookIf you are a relic like me, you may not know much about Facebook. It's a social networking site that lets you share information about yourself with friends and acquaintances. That's neat, but there's a darker side. How much information do you want other people to have about you? Do you want them to know what you've been buying recently? Users can share that kind of information with their friends and it turns out not always to be a good thing. Let's say you've bought something big for a special friend's birthday. That person is in your Facebook network and, depending on how you've set the thing up, might be able to see exactly what you've purchased with just a click or two. Bad karma. Oh—and Facebook can share that information with advertisers who pay the site. Worse karma. This week Facebook backed off a bit on the program that shares information about a members' purchases with their friends. This was a dumb idea from the start and the 23-year-old founder, Mark Zuckerberg, has apologized to members for the "Beacon" advertising program. Companies make mistakes every day. What Zuckerberg did next, though, was surprisingly refreshing. He went to the company's blog and started writing: "We've made a lot of mistakes building this feature, but we've made even more with how we've handled them." Whether he had the advice of a public relations professional or just used his own common sense is unclear, but the actions were correct if the goal was to placate clients. "Instead of acting quickly," Zuckerberg continued, "we took too long to decide on the right solution." Facebook now allows users to turn off the Beacon program that allows users to share information about purchases they make. There's nothing wrong with sharing this information, of course. That's one of the reasons the Internet is popular. But the user needs to have the opportunity to determine what information to share. And Facebook went a step further, saying that Beacon will be disabled by default. If users want it, they must explicitly turn it on. The actions came following pressure from MoveOn.org, which signed up 50,000 people who protested against Beacon. But Facebook isn't out of the woods. MoveOn says the change was good, but the larger question is the basic right of Internet users to control their own information. And the Center for Digital Democracy says that Facebook is still invading users' privacy by collecting information about what the users do on line. Let the punishment fit the crimeLet's say you're a spammer and let's say that you're making a lot of money with spam. Now let's say you get caught, tried, convicted, and sentenced. What should the sentence be? A court in Colorado seems to think that maximum sentences are a good idea. Starting on January 7, Min Kim will begin serving 30 months in prison. U.S. District Judge Lewis Babcock decided that Kim's spamming activities (for which he kept excellent records) put him in a more punitive sentencing range. The 24-year-old could be 27 or 28 when he gets out of prison. Under the federal CAN-SPAM act, Kim could have faced an extra year in prison if it had been his second offense. Investigators found 7.5 million e-mail addresses on Kim's computer and he acknowledged having bought another 200 million back in 2004. Your address may well have been in there. Mine, too. Kim earned $250,000 from spam-related activities and there was no mention in the court record of paying a fine or having to pay anything back, so for 30 months in prison, he clears a quarter of a million dollars. That's $8300 per month. This is punishment? How fast can you spell "class action lawsuit"?A lot of EVE Online players who use Windows XP and updated the game this week are more than a little annoyed because the update converted their computers into high-priced doorstops. A programming error by EVE Online, coupled with lax security settings under Windows XP, allowed the patch to overwrite boot.ini. When that happens, the computer will not boot. From the EVE Online website:
Hundreds (possibly thousands) of players didn't see the message in time, shut down or rebooted their computers, and found that they no longer had a working computer when they tried to boot it the next time. This has not been particularly well received by the company's customers. |
|||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||
| Home • Programs • Reference • Subscribe to Technology Corner News • Contact Us • Terms of Use ©2007 by William Blinn Communications. All rights reserved. |
|||||||||||||||||||||||||||||||
This is the only ad you'll ever see on this site. It's for my website host, BlueHost in Orem, Utah. Over the past several years, they have proven to be honest, reliable, and progressive. If you need to host a website, please click the banner below to see what BlueHost has to offer. |
|||||||||||||||||||||||||||||||

|
|||||||||||||||||||||||||||||||