|
|||||||||||||||||||||||||
| Previous page | Do you use a pop-up blocker? If so, please read this. | ||||||||||||||||||||||||
|
|||||||||||||||||||||||||
| Show Date: 2007.04.22 | |||||||||||||||||||||||||
Security that's not secureI ran across a report in Tweakers.net about a "secure" USB drive that isn't very secure. Losing a thumb drive with 2GB or more of personal or business data on it can be a huge problem. Those devices are small and easy to lose, so it's no surprise that a lot of them have been lost. Sipal International released a thumb drive called Secustick, claiming that it would "self-destruct" if the user entered an incorrect password more than a set number of times. The stick was commissioned by the French government (I'm thinking Maginot Line here) and a 1GB thumb drive ($175, compared to standard 1GB thumb drives at $10 or so) turned out not to be very secure. Read the entire report at http://tweakers.net/reviews/683/. The Tweakers site mentions an application called TrueCrypt, so I decided to take a look at it. TrueCrypt can encrypt the data in a file, directory, or an entire device (hard drive or thumb drive, for example) and it can encrypt it in such a way that even if you are captured and forced to give someone the password, the data will still be encrypted. Two points before I go any further: If you download TrueCrypt, read the instructions; and yes, this is exactly the kind of tool a terrorist would love to use.
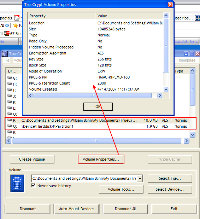
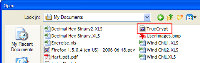
TrueCrypt creates a virtual encrypted disk within a file and mounts it as a real disk allowing encryption that is automatic, real-time, and transparent. It provides two levels of plausible deniability, "in case an adversary forces you to reveal the password." These two levels are the option to create a hidden volume and the fact that TrueCrypt volumes cannot be distinguished from random data. That is, they contain no specific header, footer, or other marker. Reading the manual for this free, open-source application made me think that I had fallen into a James Bond movie and Q had just handed me a manual for the latest high-tech device that would certainly save my life in the next episode. After installing TrueCrypt, I quickly worked my way through the beginner's tutorial and created a file on drive C. That file became an drive that I could easily mount and dismount. Mounted, it appeared in the Windows Explorer. Dismounted, it appeared only as a file. I could open the file, but nothing inside was readable. I cleverly called the file "TrueCrypt". Needless to say, this would not be a wise name to use if you want to keep data private. Nor would you be wise to choose a name such as "DebbieDoesDallas.mpeg". If you want to hide data, placing the file in a directory with a lot of other files and naming it something that won't call attention to itself ("devcache.dll", for example) would be a good choice. You know where to look for it, but nobody else would know that the file isn't a legitimate dynamic link library if you drop it into the Windows directory or the directory of an installed application. Up and running
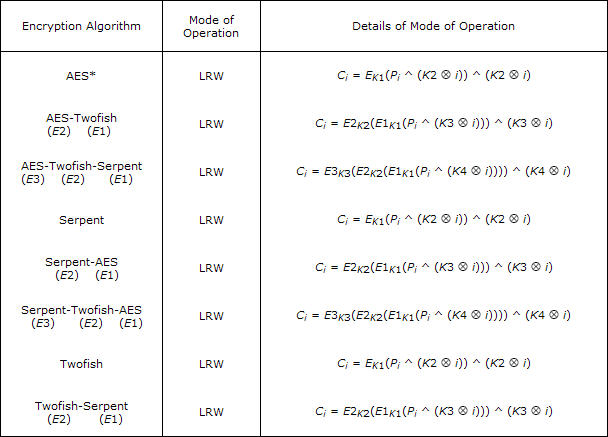
Encryption is the key (no pun intended)TrueCrypt offers several encryption methods. I present the following more or less word for word from the TrueCrypt website: AES (default)The Advanced Encryption Standard (AES) specifies a FIPS-approved (Federal Information Processing Standards) cryptographic algorithm that may be used by US federal departments and agencies to cryptographically protect sensitive information. TrueCrypt uses AES with 14 rounds and a 256-bit key operating in LRW mode. LRW mode is more secure than than the older CBC, which has been deprecated. If you are a cryptologist, this may make sense to you: Description of LRW mode:
In June 2003 the US National Security Agency conducted a review and analysis of AES, the Committee on National Security Systems announced that the design and strength of AES-256 (and AES-192) are sufficient to protect classified information up to the Top Secret level. This is applicable to all US government departments or agencies that are considering the acquisition or use of products incorporating the Advanced Encryption Standard (AES) to satisfy Information Assurance requirements associated with the protection of national security systems and/or national security information. SerpentThis method was designed by Ross Anderson, Eli Biham, and Lars Knudsen. It uses a 256-bit key, 128-bit block, and operates in LRW mode. Serpent was one of the AES finalists, but was not selected even though it appeared to have a higher security margin than the winning method. TwofishThis method was designed by Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, and Niels Ferguson. It uses a 256-bit key and 128-bit block and operates in LRW mode. Twofish was the third AES finalist. This cipher uses key-dependent S-boxes. Twofish may be viewed as a collection of 2128 different cryptosystems, where 128 bits derived from a 256-bit key control the selection of the cryptosystem. Cascades (two or more encryption methods used)These include AES-Twofish, AES-Twofish-Serpent, Serpent-Twofish-AES, and Twofish-Serpent. Thinking about encrypting encrypted files that were previously encrypted makes my head hurt, so I'll leave it up to you to research this if you find it worth your time. Simply put, the application encrypts data in a way that ensures it will be most difficult to decipher if you don't have the proper credentials. OdditiesYes, there are some.
Corruption happensYou're probably wondering what happens when part of a TrueCrypt volume becomes corrupt. When you're dealing with encrypted data, one corrupted bit usually corrupts the whole ciphertext block in which it occurred. The ciphertext block size used by TrueCrypt is 16 bytes (128 bits) so that if data corruption occurs within a block, the remaining blocks are not affected. Hardware or software errors and malfunctions can cause files stored on a TrueCrypt to become corrupted, so you should backup all important files regularly. At the very least you should backup the volume header, which contains the master key because a damaged volume header will make the volume impossible to mount. A file system within a TrueCrypt volume may become corrupt in the same way as any normal unencrypted file system. When that happens, you can use file system repair tools supplied with your operating system to fix it (chkdsk for Windows users). TrueCrypt provides an easy way to use this tool on a TrueCrypt volume: First, make a backup copy of the TrueCrypt volume (that's because chkdsk may make the damage even worse) and then mount it. Right-click the mounted volume and select Repair File system. Overall: If you need security, this is the way to get it.
The cost (nothing) and the power (amazing) of TrueCrypt combine to make this an application a must-have if you ever take sensitive data home from the office. Even FBI agents lose laptop computers, thumb drives, and guns. TrueCrypt is a good way to make sure that the data you're responsible for doesn't go astray. For more information, visit the TrueCrypt website. Odds and endsThis is the NEC section of TechByter Worldwide—the "not elsewhere classified" section. You've heard from me about TCR, the computer seller on the east side of the metro area previously. This time, you'll hear from a listener. The message is the same. If you'd like to get rid of some of Windows XP's annoying "bubble messages", I have the answer. And I'm thinking about Vista. More about TCR's outstanding sales and service policiesI've been known to grumble about bad service from companies and I feel it's important to tell you about companies that provide superior service, too. This isn't the first time I've mentioned TCR, a computer assembler with offices in Pickerington and Lancaster, and it probably won't be the last. In this case, it's not me providing a well-deserved pat on the back. This week I received a note from a listener: I asked you about a month ago about TCR. At your suggestion, my sister got her computer through them and is quite pleased with the service, price, and warranty as well as the system they built for her. They listened to what she wanted, and she got out the door at around $950 including OS and and some Office program, nice monitor, and tax, and they even downloaded and set up AVG for her. I'm sure that TCR has some dissatisfied customers somewhere, but I've never heard from one. Although TCR has built a strong central Ohio following based on listening to what their customers want, advising customers honestly, and treating customers well after the sale, the company also will assemble systems and ship them. TCR is at www.TCR.com. Shoot the nagsQUESTION: Whenever a condition is at variance with an ideal state (which itself seems to change), Windows nags me with vague and alarmist warning messages. Each time, I'm reminded of an electric sign near the airport, which has read "THREAT LEVEL ORANGE" for the past few years. Uh, yeah. Thanks for that. Windows tells me, mostly through obtrusive pop-up balloons, whether I'm connected to a network or not, whether a cable is connected or not, whether my machine "might be at risk" of unspecified problems, and on and on. How do I tell the operating system itself to shut up and stay shut? Thanks for any suggestions that will pop those (expletive deleted) balloons. ANSWER: This is pretty easy: Visit the Control Panel and click Folder Options (in the classic view). Select the View tab, then de-select the Show pop-up description for folder and desktop items option and click OK. You may also want to obtain the free TweakUI and browse through the things you can change with that tool. There's a Vista in my futureI'm sitting here looking at a box that contains Windows Vista. In mid February I wrote: I've received a lot of questions about Vista. "Should I upgrade now or later?" is the primary question. In reviewing the question, I suggest leaving out the "now or later" part—at least for the immediate future. The primary question is whether you should upgrade. For me, the current answer is no, but that's subject to change. The primary case against upgrading turns on several points: The system I have works just fine the way it is; Vista, although probably compatible with all of my hardware, isn't compatible with some of my software; no matter how well any system has been tested, there will always be problems that don't become apparent until the product is in the hands of consumers; and right now I just don't have time. But now I've decided that I owe it to you to get Vista installed and see how it works. I still won't have time to install it for at least a week, but I will install it. Prior to doing that, I asked Marshall Thompson, the head of TCR (see above), for some guidance. His reply: IMHO, Vista is not ready for prime time. There is a problem with it seeing network printers. Vista Mail is not stable. A number of installations that have been out there for awhile are starting to encounter extremely long boot and shutdown times. (Minutes, not seconds.) Second tier programs/utilities such as Nero are struggling to produce stable Vista compatible versions. Count on two GB of RAM and do upgrades only on relatively new PCs. I get the impression that software and hardware developers got tired of so many final tweaks by Microsoft that when M/S finally locked the code it was too late for many companies, large and small, to make a smooth transition. I can certainly agree with that. Computer manufacturers should continue to offer XP for those who don't want to change just yet. If you have an office full of XP machines (and many corporations are still using Windows 2000), you don't want to be forced to use Vista just yet. And for many home and small-office users, XP does everything they need it to do. Even so, I'm looking forward to seeing Microsoft's new graphical user interface. I'll let you know how it goes. Nerdly NewsThis message was not set wirelessly from my BlackberryResearch in Motion (RIM), the Blackberry guys, at first didn't admit that there was a problem. Maybe they were thinking "If we don't mention it, nobody will notice." Given the large number of Blackberry users, that's unlikely. Public relations professionals are supposed to communicate with their various publics when things go wrong and that didn't happen in a timely manner with RIM. Finally, after more than 2 days, RIM came forward with an explanation: The problem was an insufficiently tested software upgrade. Five million Blackberry users found themselves without service starting about 8 pm Tuesday and continued until Thursday night. The upgrade was expected to improve service, not to wreck it. Instead, the upgrade “triggered a compounding series of interaction errors”. At that point, anything done to fix the problem only made it worse. RIM tried to switch to a backup system, but the process didn't work properly. RIM said that the switch to backup (also known as failover) “had been repeatedly and successfully tested previously.” As for users, as of Thursday evening, your service should have been back to normal. AMD reports losses higher than expectedI've been a fan of AMD for a long time. Always the underdog, AMD was considered the "value leader" in CPUs for years, regularly providing CPUs almost as fast as Intel's, but at a lower price. AMD beat Intel briefly in the speed wars and still makes worthy products, but price cuts by Intel have forced AMD to cut prices and have created large losses. Advanced Micro Devices continues to struggle, but there are signs that the price war is abating. Consumers might view that as bad news, but it's good for Intel to have at least one viable competitor. AMD reported this week that it lost $611 million in the first three months of the year, which compares with a profit of $185 million a year ago. Sales amounted to $1.23 billion, which is about 7% lower than last year. Robert Rivet, AMD's chief financial officer, on a conference call with analysts said that the first quarter of 2007 was a terrible start to the year, but he said that AMD is "confident we have a plan to put us back on the right track." Looking at the second quarter, AMD is optimistic. Sales are predicted to be flat, but the company expects market-share gains at Intel's expense. AMD wouldn't explain the reason for their optimism, but AMD plans to cut 500 jobs, about 3% of its workforce, by the end of the year through attrition and performance evaluations. |
|||||||||||||||||||||||||
|
|||||||||||||||||||||||||
| Home • Programs • Reference • Subscribe to Technology Corner News • Contact Us • Terms of Use ©2007 by William Blinn Communications. All rights reserved. |
|||||||||||||||||||||||||
This is the only ad you'll ever see on this site. It's for my website host, BlueHost in Orem, Utah. Over the past several years, they have proven to be honest, reliable, and progressive. If you need to host a website, please click the banner below to see what BlueHost has to offer. |
|||||||||||||||||||||||||

|
|||||||||||||||||||||||||